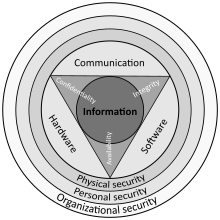
Applied Cryptography and Network Security: 7th International Conference, ACNS 2009, Paris-Rocquencourt, France, June 2-5, 2009, Proceedings | SpringerLink

PDF) Blueprint for Cyber Security Zone Modeling | Information Technology in Industry (ITII)**Web of Science (Emerging Sources Citation Index) - Academia.edu

Applied Network Security: Proven tactics to detect and defend against all kinds of network attack: Salmon, Arthur, Levesque, Warun, McLafferty, Michael: 9781786466273: Amazon.com: Books
![PDF] Design and Implementation of a Network Security Model for Cooperative Network | Semantic Scholar PDF] Design and Implementation of a Network Security Model for Cooperative Network | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a4a5ef4f2e937dc407a4089019316b054e8e3043/10-Figure1-1.png)
PDF] Design and Implementation of a Network Security Model for Cooperative Network | Semantic Scholar
![PDF] Design and Implementation of a Network Security Model for Cooperative Network | Semantic Scholar PDF] Design and Implementation of a Network Security Model for Cooperative Network | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a4a5ef4f2e937dc407a4089019316b054e8e3043/11-Figure2-1.png)
PDF] Design and Implementation of a Network Security Model for Cooperative Network | Semantic Scholar

PDF) Design and Implementation of System and Network Security for an Enterprise with World Wide Branches | Seifedine Kadry and Khaled SMAILI - Academia.edu

Evolution of Malware Threats and Techniques: a Review | International Journal of Communication Networks and Information Security (IJCNIS)



![Applied Network Security Monitoring Collection, Detection, And Analysis [PDF] [779h9gfbtph0] Applied Network Security Monitoring Collection, Detection, And Analysis [PDF] [779h9gfbtph0]](https://vdoc.pub/img/crop/300x300/3gr53f3i9cn0.jpg)